
External Attack Surface Management - EASM
EASM: Explained in Plain English
External Attack Surface Management (EASM) is all about keeping tabs on everything you expose to the internet—like your websites, servers, and APIs—so you can find and fix vulnerabilities before hackers exploit them. Think of it as a way to spot and patch weak spots in your digital armor by regularly checking what the outside world can see and interact with.
There are usually several steps:
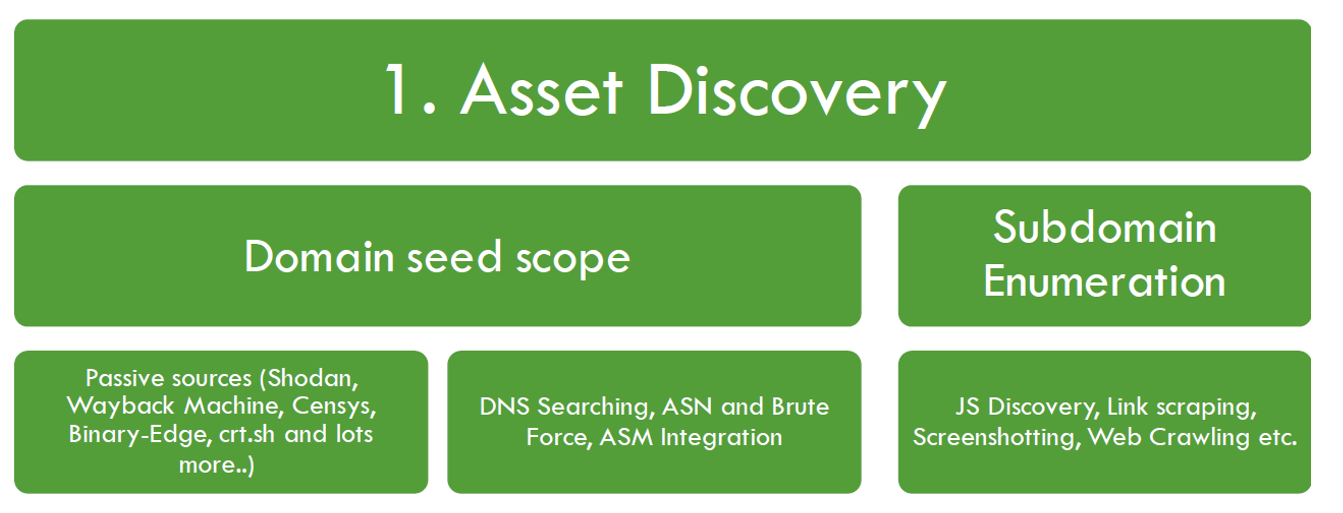
- Asset discovery - Find out all the digital things your company owns, like websites and IP addresses.
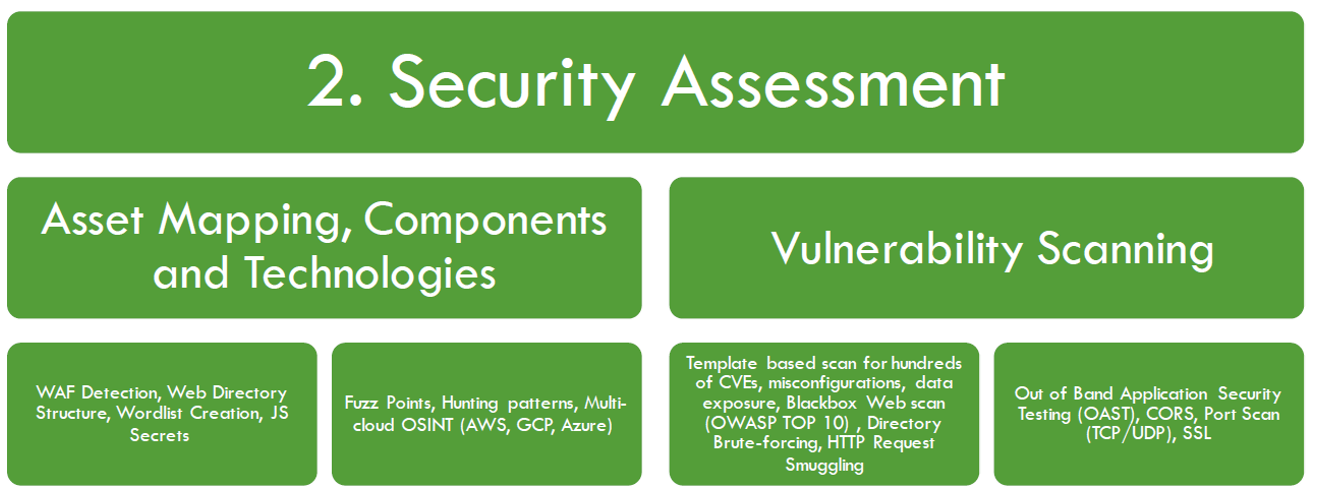
- Security assessment - Check and Analyze. Look into these assets to see if anything looks risky or suspicious, vulnerable like having old software versions or behaving strangely.
- Prioritisation - Decide which assets are most important and need immediate attention.
- Fix What's Broken- Create a plan to tackle the highest-priority risks first, followed by lower priority ones.
- And don't forget the extra step: Repeat regularly. Conduct these steps bi-annually or annually to ensure new risks are quickly identified.
K.I.S.S. - Remember: Find , Fix , Repeat!
Questions to CISO/Senior Leaders:
- How well do you actually know your external assets?
- Got a handle on what’s out there on the internet for everyone to see?
- Is your CMDB up to date, or is it collecting dust?
- How do you find and fix the weak spots in your external stuff?
- Are you keeping tabs on your attack surface regularly?
- Any rogue or unmanaged assets hanging out where they shouldn’t be?
- Confident that all your external assets are hooked up to your vulnerability scanner?
- When it comes to security, what's the stuff that keeps you awake at night?
What is Beanscan?
Beanscan offers a comprehensive suite of tools designed for scanning external attack surfaces at any scale, from small to large. Unlike traditional penetration testing—which often operates within a limited timeframe due to budget restraints—Beanscan excels in identifying and evaluating extensive digital footprints from the outset. It combines custom-built and carefully selected open-source tools to create a streamlined discovery and audit process for extensive external surface scanning. Beanscan can stand alone or serve as a valuable asset in the early stages of external attack surface management, providing a foundation for deeper, more targeted penetration testing and red team operations.
Key Features
- Unattended large scale discovery of external assets. Can be run 24/7.
- Asset discovery using seed domain, ASN and DNS Bruteforcing
- Security Assessment of external web attack surface
- Web application Vulnerabilities (OWASP top 10 minimum) including TLS/SSL Testing
- Web server infrastructure misconfiguration and tecnhnologies including CVEs
- Supports out of band application security testing (OAST)
- Public cloud enumeration for AWS, GCP and Azure (e.g., open S3 buckets )
- Dynamic Application Security Testing (DAST)
- Built in WAF Evasion
- Innovative web path discovery for unintended exposures of sensitive information using artificial intelligence (AI)
- BitDiscovery ASM Integration
- Risk and Impact analysis of discovered vulnerabilities using artificial intelligence (AI)
- Requires penetration testing exprience/know-how for maximum benefit
- Built by pen-tester for pen-testers
Breaking down its functions
Beanscan generally operates using two flows. Here are the different functions that make up the tool:
What is Redbean.AI?
Redbean.AI is a core part of Beanscan but can be use separately. It's an efficient tool designed for fast port and vulnerability scanning, particularly suited for unattended, 24/7 wide-scale vulnerability assessments where time is a critical factor. It combines custom-written tools with carefully selected open-source community tools to support both web application and infrastructure scanning. The tool leverages artificial intelligence (AI) to guide more effective remediation of vulnerabilities, boasting over 2,000 testable CVEs and continuously growing. Redbean.AI benefits from quick releases and up-to-date proof of concepts (POCs) contributed by thousands of community security researchers worldwide. It is primarily used in penetration testing engagements where traditional UI tools like ©Nessus or ©Nexpose/InsightVM are unavailable or used in combination. Additionally, it supports AI-generated HTML reports, enhancing the overall efficiency and effectiveness of the scanning process..
Why another vulnerability scanner?
Redbean.AI started as an in-house tool to address delays found in commercial scanners' update cycles. These tools often require extensive testing to ensure updates don't disrupt existing applications, slowing down the release of proof-of-concept (POC) code for vulnerabilities. As scanner backed by community however, leverages thousands of volunteers and researchers, enabling it to use POC code for newly discovered vulnerabilities much faster. The quicker we have POC, the quicker we can identify and resolve vulnerabilities, avoiding the extended wait times typical of commercial products.
According to Cloudflare's Application Security report for 2024 , Threat actors are fast to weaponize available proof-of-concept (PoC) exploits in real attacks, sometimes within just 22 minutes of the exploits being made public. Therefore, we need a faster way to detect and close new vulnerabilities too.
Free to use, what's the catch?
Our usage is free, so you might wonder about the catch. Instead, consider asking: why pay for features you may not need? Commercial vulnerability scanners can be pricey, from thousands to even hundreds of thousands of dollars. This cost often includes a range of bundled features, many of which you might never use. If you’re looking for a straightforward tool just to identify vulnerabilities, community backed scanner options such as Redbean.AI can be a solid and cost-effective alternative. We recommend evaluating your organizational needs and budget to choose the best option. There's nothing stopping you from using both, as each tool can complement the other. Give this tool a try; it might work well for you. If it doesn't fit your needs, you can always explore other options. It certainly worked for us!
Download and usage
Visit the github page for details. Reach out if needed!

